Civil airport refers to a demarcated area dedicated to the take-off, landing, taxiing, parking, and other activities of civil aircraft, including ancillary buildings, devices, and facilities. The main role of the civil airport is to allow the aircraft to take off safely, surely, and quickly, safely and reliably carrying passengers and cargo. Safeguarding the safety of the flight area, terminal buildings, auxiliary facilities, passengers, and staff has become the main goal of airport security systems.
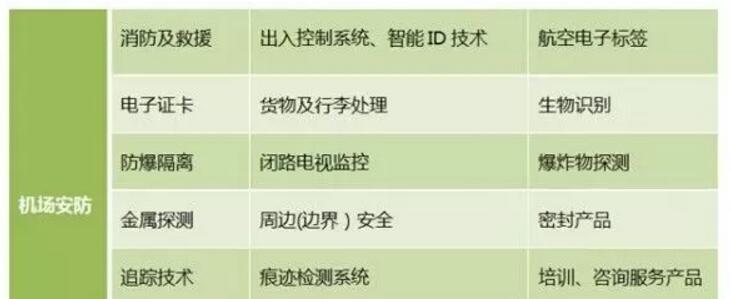
Airport security includes but is not limited to the following subsystems:
At present, most of the above-mentioned security subsystems have been applied at airports, but most airports are still in the stage of independent operation and maintenance of security subsystems. The status quo is summarized as follows:
Diversified and isolated security subsystems, with different styles of operating interfaces, lack of an integrated and unified management perspective, and poor interoperability;
Various security subsystems generate a large amount of business information and are intensively pushed to users. It is difficult to rapidly synthesize information and judge events.
The response and resolution of security incidents requires human judgment, lack of a unified best-in-class action plan, and affects the security of the system;
The cumbersome and decentralized evidence collection process needs to be performed within different systems. It cannot be effectively aggregated and a panoramic perspective of the event cannot be given.
The security integration technology can combine the above subsystems into organic linkages based on needs. Each has its own emphasis, is relatively independent, and complements each other, thus forming a variety of means, multiple defense lines, set without death, separation without separation, security and reliability. The complete and flexible management system ensures that the technical system is truly managed and the security is guaranteed.
Perfecting the security system should comprehensively consider the characteristics of the airport, the areas to be guarded against and the need to guard against the specific structure, layout, and functions of the buildings, ingeniously and flexibly set up different defense systems, and combine them together rationally and organically to make these technologies The system maximizes its role in the security and management of airports.
The security integrated system is the core of airport security, the bond of various security subsystems, and is a necessary measure to improve security capabilities and speed up response and disposal.
Application form of airport security integration technology
Based on the current status of airport security construction, a security integrated platform based on and above the security subsystems of the airport should be built to realize the application of integrated technology.
The platform mainly completes the following tasks:
Unified publication and management of information
The security integration platform is an open integration platform that realizes the linkage commands among subsystems in the physical protection system and controls the unified release and management of information. The subsystems that the integrated platform can link include: video monitoring system, detection alarm system, entrance and exit control system, security communication system, security lighting system and so on. At the same time, keeping clock synchronization with the master clock system ensures that several business applications of the integrated management platform run on the same clock reference.
Information exchange and linkage control
The security integration platform needs an open architecture and advanced system integration technology to perform data collection, linkage processing, and comprehensive monitoring and management of the integrated subsystems. It is the core and integration platform of the entire physical protection system. The system should be integrated with each subsystem to complete the information exchange and linkage control between the systems. When there is an emergency, follow the pre-arrangement rules and carry out linkage processing.
Open, loose coupling interface mode
The security integration platform and the interfaces of each subsystem should adopt open standard protocols to implement open and loosely coupled interface modes. Each sub-system is a product of a different manufacturer and has a greater diversity and closeness. Therefore, the business logic of non-cross-subsystems is implemented within each sub-system. Only the business logics across sub-systems are implemented on the integrated management platform. The independent subsystems are integrated on the basis of full play of the existing functions of the subsystems, highlighting the advantages of integration.
Centralized alarm display, positioning and unified processing
Through the security integrated platform to handle incident control and processing, the user can define the level of alarm events, alarm linkage process, alarm event processing, alarm display and prompt information, etc.; when an important alarm occurs, centralized display, alarm positioning, unified deal with.
Equipment operation and maintenance
Through the security integration platform to provide various types of equipment classification, group management, set the device display status of different states, define the device's static property information. In addition to implementing device configuration management, it is also possible to manage device operation status.
3, security integration platform integration technology
Integration concept
The first is the integration of system technologies. Modern security not only adopts various common acoustic, optical, and electrical technologies for security protection, but also adopts an IP network connection architecture to further introduce various advanced technologies and implement these technologies. Integration to form a large-scale, multi-faceted security system.
Followed by the open concept, the security integration platform needs to provide a unified interface service layer and have a series of application interfaces that meet commercial standards so that products can be interchanged and interconnected, and the security integration platform can be changed as needed.
Finally, the concept of the platform, security integration work needs to integrate a large number of IT technology and related systems, equipment, which is quite difficult to grasp and use. Therefore, consider quickly building and enriching various application systems based on a framework. It is recommended to provide a security integrated application server framework with flexible configuration of functional modules to support the processing, exchange, and release/control requirements of various information integrations.
The open security integration platform is actually a platform that carries typical security technology components. It can expand the development foundation or framework according to the needs of users. System developers can focus on and meet the needs of customers and turn these common underlying technologies into It is realized by an integrated platform. The system integration platform itself follows the principle of openness and can be continuously improved and developed.
Hierarchical structure
As shown in the figure, from a large perspective, the security integration platform can be divided into three levels. The bottom layer is the data resource layer integrated with the security system, the middle layer is the middle application layer integrated with the security system, and the top is the user service layer integrated with the security system.
The physical protection subsystems at the data resource layer operate independently and implement internal business processes on their own. The security integration platform server at the middle application layer only has data interaction and no functional coupling. The operation of the middle layer does not affect the physical protection layer at this layer. The system is working properly.
The security and integration platform server of the middle application layer can accurately respond to the cross-system security integration requirements of the users through the initialization and on-line configuration of the supporting management tools, realizing message exchange and device linkage of the physical protection subsystems, and providing upward security man-machine interfaces. Required function interface for device operation status notification and device management control.
The user business layer is the final human-computer interaction interface of the security integration platform. The security integration platform client is different from the supporting management tools of the security integration platform server. It does not have detailed configuration functions such as interface parameters and operating parameters, but it has stronger services. Sex can monitor, control, and manage all visible and controllable security devices in a unified manner, and can quickly and visually define information exchange or device linkage rules across systems.
Key technologies
Interface adapter/external gateway
The interface adapter/external gateway module is an integrated access layer functional component of the security system. It is responsible for the message interaction, data cleaning and conversion and the necessary distributed service processing functions between the external business system and the integrated platform, automatically differentiating external systems. The integrated interface is converted to a unified interface specification to access the internal message bus.
The interface adapter/external gateway module shields the differences of the technical system downwards. The interface adjustment of a technical system is even the replacement of the device brand. It is only necessary to replace the corresponding access adapter, without affecting or touching the upper-layer architecture. Availability and stability.
Reliable message exchange
The exchange of messages reflects an interaction between various functional components or application functional subsystems in the system. The message exchange module provides a bus exchange mechanism for messages. As long as the parties involved in the communication body incorporate the message bus, there is no need to force the message sender to know the information of some message receivers, nor does it force the message receiver to know certain message senders. The information, the message sender and the message receiver only need to know the format of the message and the destination to be reached to achieve mutual message exchange.
The message exchange module is mainly composed of message routing management and message exchange engines, and provides message security authentication and connection heartbeat management to ensure the legality and stability of the external system access message bus.
Business linkage processing
System interconnection, mutual control and online transaction processing are the most significant features of the integration server. The business processing module of the integration platform is responsible for the completion. In order to cope with the different needs of the online transaction processing and equipment planning interactions integrated by different security subsystems, business processing services are designed based on the concepts of flexibility, reliability, and scalability.
The business processing module is based on a preset event-prescription association rule. After the business processing engine receives the instant information, it is automatically addressed and directly transferred to the corresponding business component to perform on-line data processing or trigger a linkage plan. According to the business process pre-set by the system, the business processing engine distinguishes different imported signals for event-prediction triggering, and executes all the linkage policies corresponding to the signal. The implementation process can be based on user needs to join the manual confirmation link, prompting the user to fully understand the results of subsequent system operations and confirm that the operation is safe and feasible.
4. The business core of security integration platform
The ultimate goal of building a security integrated platform is to improve the management level and improve the processing capacity of the emergency time. From a business perspective, emergency handling and scheduling management mechanisms are the core of the security integration platform.
A mature emergency management and scheduling management mechanism needs to have three points:
The first is a perfect plan library. This is an important function of the security system integration platform. According to possible events, it lists all possible emergency treatment plan libraries according to classification, location, time slot, and severity, and continuously improves and optimizes.
The second is the effective information that command and management personnel can obtain. The security system can provide real-time video information, alarm information, and geographic information. Historical information relies on fast and intelligent search tools. Making full use of various information sources is an effective means of assisting commanders in decision-making.
The third is effective drill training. After the system is built, it usually pays attention to the basic operation and management training, and neglects the training of emergency handling dispatch. In the event of major emergency incidents, command and dispatch personnel at all levels are still at a loss when the system provides various types of plan guidance. Regular emergency dispatch exercises can not only familiarize managers at all levels with the preplan, make reasonable choices, but also can optimize and improve the preplan, and further effectively improve the level of emergency command and dispatch.
5, the development trend of airport security integration technology
The Internet of things, big data, and cloud computing technologies will bring about fundamental changes in airport security integration. Airport security integration technology will develop toward more and more intelligent systems.
For the security integrated system, the completion of data business is mainly realized by the integrated platform data acquisition and data storage analysis system. The integrated platform needs to realize the human-computer interaction function, while the big data system mainly realizes data storage and data analysis functions. After various types of front-end data are transmitted to the back-end system through the network, some can be displayed directly on the platform, such as real-time video images, and some need to be displayed through simple processing of the platform, such as related alarm linkage, intelligent alarm services, etc. Those who need to do background mining through big data, use the specific algorithm that meets the scene after analysis and calculation, and then show through the platform, such as behavior analysis, feature analysis, through rigorous statistical modeling, to achieve after-event analysis and pre-event The effect of the sentence.
6. Conclusion
Airport security integration involves a wide range of systems, diverse monitoring objects, and complex business scenarios. These characteristics determine the complexity and inevitability of airport security technology integration. The security integrated application platform is becoming an increasingly important part of the airport security system. Along with the technological revolution and application changes that occur time after time, it will develop in a more open and smart direction. The traditional isolation and lack of linkage subsystems will be integrated. The security platform replaced, the various subsystems will be closely connected together, and the systems will be linked with each other through integrated technologies to form a "Daan Security Platform" system. The security integration technology will develop in the direction of deep integration, full integration, and seamless integration. The future airport security integration system will be more intelligent and more powerful.
Hoods For HYUNDAI:
Yangzhou Gemini Vehicle Industry Co., Ltd. has more than 20 years experiences in producing and selling metal body parts of various vehicles. We are specialized manufacturer of Hoods used for HYUNDAI, including ACCENT, ELANTRA, CRETA, SONATA, TUCSON, SANTA, MISTRA, STAREX, I10, ATOS, I30, and H100 PORTER. We own Hydraulic Machines, Punching Machines, Numerical Control cutting Machines, CNC Grinding Machines, Painting and Electrophoresis Coating lines. We provide "Professional Efficient Effective" service to all of our domestic and oversea customers. We are very glad to be contacted by you and hope that we can keep a long-term cooperation on the business of Steel Body Autoparts.
Hoods For HYUNDAI
HYUNDAI Hood,Carbon Fiber Hood HYUNDAI,Used HYUNDAI Hood,HYUNDAI Glass Hood Car
Yangzhou Gemini Vehicle Industrial Co., Ltd , https://www.yzqsap.com
![<?echo $_SERVER['SERVER_NAME'];?>](/template/twentyseventeen/skin/images/header.jpg)